Trust Center
Security
Safeguarding your data is our top priority.
Veritas is committed to transparency around our development practices and management of security vulnerabilities. We put security at the core of our product development, infrastructure, and processes. Read our Vulnerability Management Commitment and Disclosure policy to learn more.
A Message from Christos Tulumba, CISO
Veritas takes security seriously and prioritizes the protection of our products and enterprise assets. Our comprehensive approach ensures that we address all aspects of security to maintain a secure environment for our customers and partners. Trust Veritas to uphold the highest standards of security and safeguard your valuable assets.
- Secure product development and testing
- Identity and access management
- Cloud security
- Endpoint protection
- User and communications security
- Vulnerability and incident management
- Secure logging and monitoring
- Security governance and risk management
- Supplier risk management
- Security culture and training
Secure Software Development
Security begins in product development, where we use secure coding methods and analysis tools. Veritas products undergo penetration testing by an independent third-party firm at least annually. The Product Security Group (PSG) also conducts internal scans as part of the release of a new product version. PSG manages schedules for pen testing and internal vulnerability scans. Our Secure Software Development Framework is modeled after NIST SP 800-218, a core set of software development practices focused on mitigating vulnerabilities.
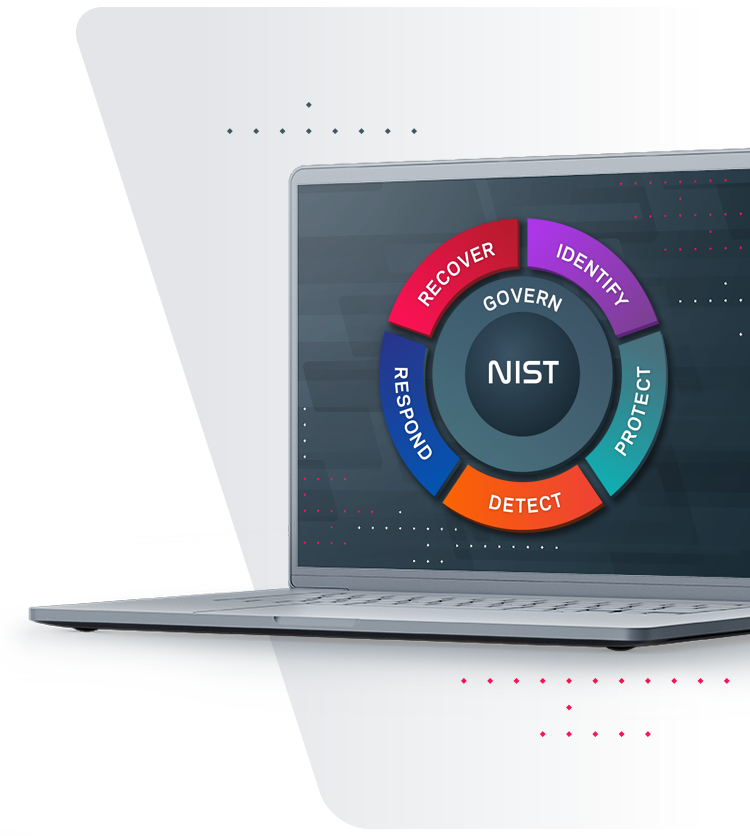
National Institute of Standards and Technology
Veritas aligns to the National Institute of Standards and Technology (NIST) framework—a standard that addresses cyber resiliency as five key pillars: Identify, Protect, Detect, Respond and Recover. Ultimately, we measure ourselves with a simple question: Do our solutions and actions result in better protection of the world’s data and infrastructure?
- Secure by Design: We design and build products in a way that reasonably protects against malicious cyber actors successfully gaining access to devices, data, and connected infrastructure.
- Secure by Default: Our products are resilient against prevalent exploitation techniques out of the box without additional charge.
As the threat landscape continues to evolve, you will continue to see innovation in both areas to ensure we’re driving the right outcomes with simplicity for our customers.

REDLab
Veritas REDLab is a fully isolated, in-house security lab where we proactively validate our cyber resiliency capabilities, including anomaly detection, malware detection, and product security posture. We test Veritas software against the world’s worst malware so you can be confident in the ability of our solutions to protect you from unexpected downtime, data loss, and data theft.
Reliability and Resilience
Unmatched in the industry, Veritas incorporates data sovereignty, granular non-disruptive recovery rehearsals, and multi-cloud IT resiliency orchestration (ITRO) at scale. We use cloud service providers (CSPs) for application resiliency in our cloud services in regional, across regions, and across CSPs. Veritas cloud-native tools enable you to create services in a highly resilient fashion and ensure high levels of availability and resilience. We offer real-time status updates through our cloud service availability.
Technical Alliance Partner Integration
Data security is a team sport—no single product addresses all aspects of security requirements. At Veritas, we partner with the best across the industry to optimize your investment by ensuring our products not only integrate well, but also stand up to cyber attacks. We ensure minimal downtime, fast recovery rates, and seamless restore to a clean copy.
Through these strategic partnerships, we deliver industry-leading solutions across a range of areas, including:
- Antivirus
- Authentication
- Encryption
- Key Management Systems (KMS)
- Immutable storage
- Privileged Access Manager (PAM) solutions
- Security Information and Event Management (SIEM)
- Security Orchestration, Automation, and Response (SOAR)
- Extended Detection and Response (XDR)


